Home » Research » About » IT vs OT | When Facing The Insider Threat | What Happend | Free Software vs Open Source | ask me |
What if a pretender could be ANYONE... then you could have so many and interesting episodes that the show could last for a long time.
Insider threats are dangerous. Because often times these attackers know how the system is configured and know its weaknesses. Hackers like insiders can compromise a seemingly unimportant system to access the network and use it as a launching pad for attacks on other systems and many people would be none the wiser because they don't have the proper controls to prevent and detect malicious use. Asking the companies about the most typical way they will be compromised, most answer this that it will be an inside employee. One of the most important communication channels between the private sector and the government are the Information Sharing and Analysis Center (ISAC) ★ Insiders are without a doubt the largest threat. They know where the crown jewels are. They know the processes on the inside. They already have logins. If they have something to gain, there's not much prevent them from doing the wrong thing. The attacker who has the strongest position into an attack is the trusted employee. ★ What's become more and more important is to know the starting point of an attack.
Social engineering and phishing have long been one of the most popular methods for cyber criminals to break into a corporate network or steal sensitive information. These methods are just as popular because they target the weakest link in your security: humans. Even the best security tools cannot protect you when your employees (unknowingly) open the door wide. Therefore, invest in awareness and commitment first, then the rest will follow automatically. ★
Social engineering attacks take place on two levels: the physical and the psychological. ★ First, we'll focus on the physical settings for these attacks: the workplace, the phone, your trash, and even on-line. In the workplace, the hacker can simply walk in the door like in the movies, and pretend to be a maintenance worker or consultant who has access to the organization. Then the intruder struts though the office until he or she finds a few passwords lying around and emerges from the building with detailed information to exploit the network from home later that night. Another technique to gain authentication information is shoulder surfing - to just stand there and watch an oblivious employee or secretariat type in their password.
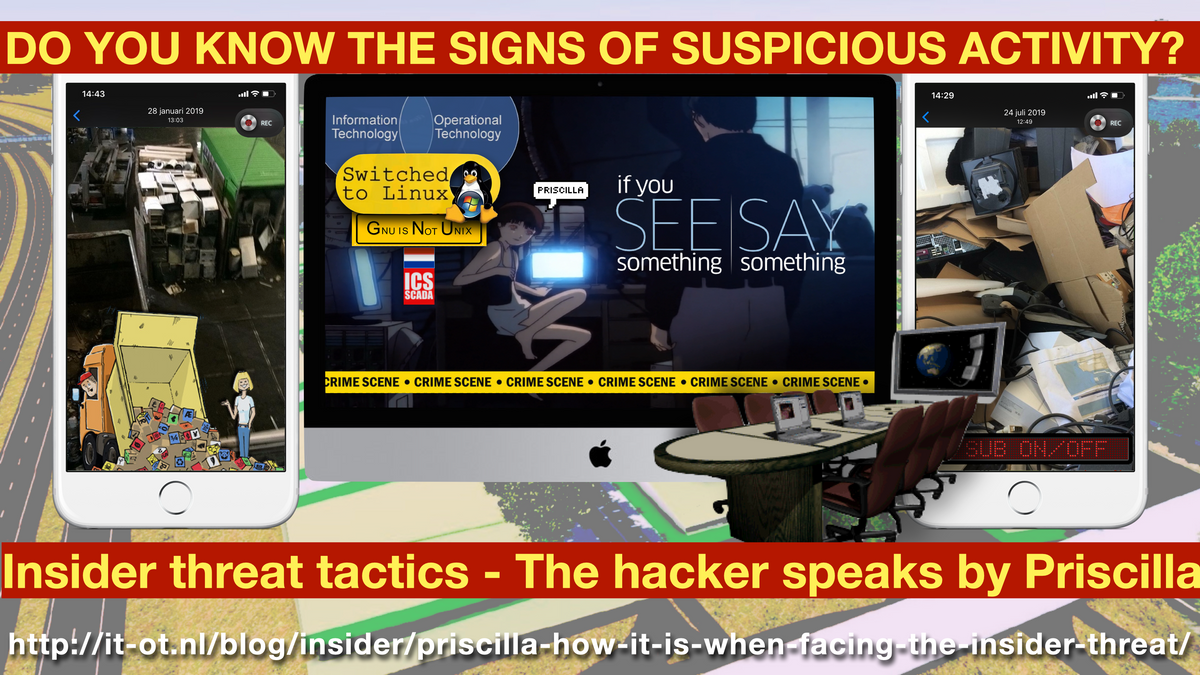
PRISCILLA: How To Steal Confidential Data - Insider threat tactics - Government of Electronic Recycling - Wednesday 24 July 2019 - The hacker speaks by Priscilla F. Harmanus, 1993 from the Netherlands.
Other guises used by social engineers are to pose as a computer aide or helper, and try to gain information as you fix the computer. ★ This technique, however, relies on the assumption that there is something wrong with the computer system. By posing as a helper, the legitimate user will be less suspicious and more willing to answer your inquisitive questions. Another form for the attacker to take is that of a system operator for the network itself. The potential hacker will pretend that an error in all accounts has made, and he needs to reset the accounts. In order to do that, he needs the old passwords of the users. If the employee is naive enough, he or she will divulge the information, thinking that hey are doing their company a service. Although there are many other methods and techniques, these previous examples account for most recorded incidents of social engineers.
According to Methods of Hacking: Social Engineering, a paper by Rick Nelson, the three parts of reverse social engineering attacks are sabotage, advertising, and assisting. The hacker sabotages a network, causing a problem arise. That hacker then advertises that he is the appropriate contact to fix the problem, and then, when he comes to fix the network problem, he requests certain bits of information from the employees and gets what he really came for. They never know it was a hacker, because their network problem goes away and everyone is happy.
✓
Insider threat tactics: The hacker speaks by Priscilla
· Priscilla Felicia Harmanus · 1993 from the Netherlands · Last update: 27 aug 2020
How I discovered Free Software and met RMS ★
No one knows who I am yet and what kind
of content I produce. So why not focus on a topic that
people are already searching for, right?

.png/picture-1200?_=174134b4c80)